Why 2024 Could Turn Out To be a Pivotal Bullish Year for Crypto
Those early examples, though, were through closed networks and the actual exchanges of money and goods generally had to take place in person. NEMESIS Premium RCA Cord is one of the best cables available on the market. Just offer a service that many people want and news about the service will spread via mails, messages etc. Additionally, operational security OpSec Nemesis link best practices, such as using disposable email addresses and avoiding revealing personal information, are crucial for maintaining anonymity. The first part of this domain name is a 16 character string numbers and letters only that is derived from the hidden service’s public key. 🌀 BrowserBox is secure reverse proxy that empowers web app virtualization via zero trust remote browsing and a secure document gateway. Servers configured to receive inbound connections only through Tor are called hidden services. Assistance was also provided by the Justice Department’s National Cryptocurrency Enforcement Team. Use every means at your disposal to cultivate strong, direct relationships with retailers. D’s, Wall Street Market, and Tochka Market. As a result, the forum is still active, but its future may seem uncertain. We ensure the database’s relevance by incorporating information about fraudulent brokers that users report to us, after conducting a thorough analysis ourselves. We update our DeepOnion to EUR currency in real time.

Slope Takers in Anonymous Markets
Contact us to find out more about Elliptic’s cryptoasset investigation and compliance solutions. In more technical terms, the dark web is the part of the web where sites are hosted on so called darknets — computer networks overlaid on other networks. A: The surface web includes publicly visible websites blogs, shopping sites, news sites, YouTube. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Attacks typically target users of banking, cryptocurrency, e commerce sites, and even email. The Tor Browser is the only way to safely access. Over the years, dozens of large DNMs have been established and eventually shut down by law enforcement, including AlphaBay, Dream Market, Wall Street, and, most recently, Hydra. For more information on our use of cookies, please see our Privacy Policy. Prices range from as little as $10 to $500 or more for some data. DeepOnion is a cryptocurrency that is highly volatile and therefore may not be suitable for all investors. Only users who have a paid subscription or are part of a corporate subscription are able to print or copy content. It claims to be secure to the extent that not even Hushmail employees can read the contents of user emails. Before the introduction takes place, the client in this case, you picks a Tor relay and establishes a circuit to it.

DeepOnion Price ONION
In this new commentary, CEPS Director Daniel Gros argues that the weakening of European demand triggered by austerity is the real cause behind the recent deterioration of emerging markets’ current accounts. El Salvador to host 44 countries to discuss Bitcoin. Another vendor emphasized that having multiple storefronts minimized any concerns about a market going down: ‘i have plenty of backup storefronts already active and my customers will know how to find me not super difficult. Nemesis market is awesome. Read the article here: ryptocurrencies LawEnforcement DigitalAssets Hackers Hacking. If CitEc recognized a bibliographic reference but did not link an item in RePEc to it, you can help with this form. Over the years, dozens of large DNMs have been established and eventually shut down by law enforcement, including AlphaBay, Dream Market, Wall Street, and, most recently, Hydra. Crude is higher in the O/N session $79. Onion sites, which provide anonymity to users and websites alike.

Read The Nemesis The Diabolic Book 3 by S J Kincaid
And you don’t even need an account for that – simply visit the site and browse. Hydra also featured numerous vendors selling false identification documents. These companies included Ltd. 5% of onion addresses can go offline. This setup isn’t ideal for some use cases, but for me it has allowed me to vastly improve the resilience and disaster recovery time of my infrastructure, without posing an undue risk to my Hidden Service private keys. Verified onion links updated 2024. Check if you have access through your login credentials or your institution to get full access on this article. Every DNM lifetime is limited and because of this business character every one of them will eventually make an exit scam or will be seized by law enforcement. Further, we include a small case study on darknet marketplaces to demonstrate how reports concerning the number of a certain category can easily mislead. Rely on our team of analysts to monitor your adversaries and engage with threat actors. In light of recent busts, however, dark web operators have increased their vigilance and are scrutinizing applicants more thoroughly. Only extremely large volume going through a particular broker may tip off other participants who know that certain clients trade with that broker. “The migration of vendors, plus the timing and source of OMG’s initial revenue suggests that Hydra administrators may have been involved with the development of OMG. Methods like search engine optimization and other marketing techniques cannot be used either as they aren’t part of the clearnet. 3 million dollars when they shut the market down. Journal of Finance, Forthcoming. The market took more than 50% of the market share in April and May, reaching a peak of 65% on April 23. Two weeks after the takedown of the Dark Web marketplace AlphaBay, its successor Hansa Market was also closed as part of a coordinated operation by the Dutch National Police, Europol, the Federal Bureau of Investigation FBI and the US Drug Enforcement Agency DEA. Starbucks teases Web3 platform in NFT announcement.

Features delivered by the DeepOnion team:
Today web site screen shots below. “The Justice Department will be relentless in our efforts to hold accountable those who violate our laws – no matter where they are located or how they try to hide their crimes,” said Attorney General Merrick B. Much of the plastic discarded by the public winds up in rivers, streams and oceans, where it can remain for centuries, choking wildlife and ruining natural habitats. Many search engines and even Facebook provide service over Tor for countries with heavy censorship. Easily learn how to use it for your highest rewards. Now you’ve surely filled out many captchas in the past, but we like to think ours are a little more, shall we say, entertaining. Compared to exchange trading, this increases the flexibility of OTC trading, but also increases the risk. Stock Broker SEBI Regn. Rob keay verified owner – 02/08/2022. And that’s not the only tightrope to walk. Metrics record slightly more than 60,000 unique.

Hot Network Questions
When it comes to digital assets, advisors should ask themselves the following two questions: one, why crypto and two why now. Nemesis is under DDoS Attack. The seizure of the Hydra servers and cryptocurrency wallets containing $25 million worth of bitcoin was made this morning in Germany by the German Federal Criminal Police the Bundeskriminalamt, in coordination with U. D’s, Wall Street Market, and Tochka Market. Matrixport, which bills itself as a crypto financial services firm, released a note last week projecting bitcoin would reach $63,140 by April 2024 and $125,000 by the end of next year. At the other side of the English Channel, the idea of a liberalized and internal electricity market for Europe started taking shape in Brussels. Instead, they are retiring voluntarily, and in an orderly fashion. The vendors openly advertised their drugs on Hydra, typically including photographs and a description of the controlled substance. “This was the Amazon dot com of the dark web,” a Justice Department official said. In contrast, out degree centralization captures the extent to which a few markets send the majority of ties. Currently, the market supports four cryptocurrencies: Bitcoin, Monero, Litecoin, and Zcash. Together, these covariates offer different insights into the local processes that dictate collective patterns in vendor flows. If so, then you must explore the capabilities and efficacy of Crypt Design. Vendors on Hydra also offered services such as “Hacking for Hire,” “Ransomware as a Service” “RaaS”, and a myriad of money laundering features. Users put forward a number of theories to explain the mysterious takedown, which ranged from technical issues to a public crackdown or even an exit scam where administrators shut down the site and take off with the money, a common Dark Web occurrence. Fail is supported by our users. In the meantime, please connect with us on social media. This is a popular dark web site that peddles software exploits which hackers can use to break into your computer or network. Our easy to use Setup wizard allows you to build a distributed grid for your enterprise in minutes. Learn how IP addresses and subnets work, and compare. You can update your choices at any time in your settings. A host is basically a website’s house, or where it lives and takes up space. Once those three Tor circuits are in place, the hidden server can publish the data necessary to connect: the introduction points and the identifying data required to cryptographically assure that communications directed to that hidden service arrive there. Unfortunately I was in the hospital and couldn’t report a problem in time. Central African Republic adopts bitcoin as legal currency. Onion browser: A web browser like the Tor Browser Bundle TBB. After G20, investors, speculators and dealers are convinced that cash cow Ben and his foreign counterparts will provide the necessary liquidity at low cost well into 2010 or beyond. We estimate the likelihood and intensity of ties forming between markets using two classes of predictors: nodal covariates and structural covariates. Leverage the broadest and deepest coverage of dark web sources to gain visibility into threat actors and their activities. If you want artisan items, contact the artist yourself.

60+ courses and career paths – Flat 30% off on learning plans, use code NEWYEAR
After that, both the client and the hidden service can use their synchronization point connection chain to communicate with each other. J CODE entities, including the FBI, U. Treasurers and CFOs are worried about how their FX tech will cope with a potential increase in hedging activity. Step five: – the Hidden service decrypts the client’s message and finds the address of the synchronization point and a one time key. The Tor network understands these addresses and can route data to and from hidden services, even to those hosted behind firewall or network address translators NAT, while preserving the anonymity of both parties. Ahmia is another dark web search engine. That said, scanning services typically comb through data available on many places in the dark web, and while the results may not be complete, they can be useful. Crypto market stuck for now, but Bitcoin to make new all time highs within 24 months: Coinshares’ CSO. Here’s what you can you do if your information is found on the dark web. In general, the complete connection between client and Onion Service consists of 6 relays: 3 of them were picked by the client, with the third being the rendezvous point, and the other 3 were picked by the Onion Service. Not Evil has more than 32 million websites and addresses indexed from Tor servers, as well as more than 14 million onion links. The deep web is about 90% of the internet, while the dark web makes up about 5%. BTC and ETH outperform traditional markets in July despite the dollar’s strength. We don’t recommend connecting to the Tor browser without one. “A number of investigations to identify additional individuals behind dark web accounts are still ongoing,” Europol said. Before customers can connect to service stations, it must declare its support in the top network. Crypto transactions are supposed to be secure and irreversible — whoever holds the cryptocurrency key is effectively the owner. Earlier in the year, law enforcement agencies had managed to take down a big platform known as Wall Street Market. Working dark web links 2024 update. As a bonus, ProPublica is one of the most polished web experiences you’ll have on the dark web. On these marketplaces multiple vendors can sell their products and services on different categories over these platforms and get rated by their users. Understanding PGP usage in this context is important, but can be overwhelming for newcomers. “It tended to be very civil, very high level discussions and now, you’ve got every man and his dog on there. Among the selection of tools and data hackers can buy here are dumps of stolen credit cards, stolen credentials, access to specific remote desktop protocol clients/servers, and stolen cookies. Site design / logo rev 2023. The emergence of Telegram as a new dark web frontier also partly explains the revenue reductions in traditional dark web marketplaces. Finally, a common narrative consists of categorizing a large portion of onion services as marketplaces.
You are currently on corporate access
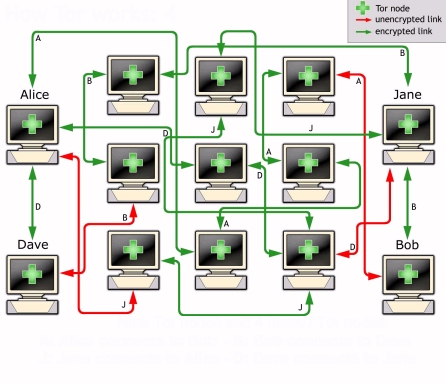
Other than the database that stores the hidden service descriptors, Tor is decentralized by design; there is no direct readable list of all hidden services, although a number of hidden services catalog publicly known onion addresses. Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. Some mainstream publications such as the New York Times maintain a presence on the dark web for just such tips, and other publications around the world maintain a presence to circumvent government imposed internet censorship. Fill out the form to speak with our team about investigative professional services. Rating services are increasingly popular since dark web marketplace “exit scams” remain high. The Hidden Wiki doesn’t discriminate, so if you start diving into dark net links randomly, you may come across objectionable or dangerous material. The seizure of the Hydra servers and cryptocurrency wallets containing $25 million worth of bitcoin was made this morning in Germany by the German Federal Criminal Police the Bundeskriminalamt, in coordination with U. Malware, stolen data both personal and enterprise, ransomware leaks, cracked software and even abuse content are all things not exclusive to opaque. BEGIN PGP PUBLIC KEY BLOCK mQINBGFQAzoBEADEu8JiUaH+4QtAQdmxi9Bt43RCgyCeeXdZH0dJrYTDRalyXAK5S4Zj1SjoNp5lGJhpKuctNT/ectksyztZ+2MWarjXqPccVD2+ByX0gWbdf1DACxbddYwwnn/DCa9RDNbApUM5VyhMt5Nq7omOLT7n7tpof0F9YYbumvfqtNSz7/fkUikMUhU3QTWj8EbQ9T21p95GqMvHFVsIz6CZTI4ts6GfWuQjUKxFJD1deuI/jaEgBBxWDEhN0LnWwT6bXWGdy2UayYB/MkopHo9EV08lEBmmUH9q391SZDgzIq4w1d7rHNVydMG0ACDd2h0wZZlSTSkxD8L+AFgKmBairYaRb+p9SfVAAOlgE2Wh0DnaCrVA532WPqfEacvDf0TxVHUxyHDGVenzkcKAanFGJMFOdj2jdlSaCrJ+M128YKRSHH7MJUee1mDmwwztvNypE9FXVr9ADbldbsvu+EGrF8beWoCMdE/7liHHcISOwewByn7MgnCHktTm6EEKfoUw/i5N8ReMG7wUV0nsaYLNBTi9vj5sticIzziqLSnyODizG7KBiNVDXwhFR1GLdDovAhLsfIxm1V7KA7qqITnqcP8reuvbdmvAQ0ogEuhIh9OCdb7jbywBwIIhN0PDfSZbQvlwEEUxA9AvPKVGIKs06YAJKEQveijJbzfq4pHfUV4SPwARAQABtA5OZW1lc2lzIE1hcmtldIkCTgQTAQgAOBYhBIOOXh30MAIQEZ0/3Pq+3aguobTFBQJhUAM6AhsDBQsJCAcCBhUKCQgLAgQWAgMBAh4BAheAAAoJEPq+3aguobTFatgP/2ziO9D8UkJC0xH5yKcdBhlVqKKtIU2D9LCrZ/Hs627vKZ9WdzU0uqb+Re1ur4QBIqTvwwHAkicaP2zPhAwdW1pPKsAkaGQOr3yTPs/cVQNIoG7HiTJqDzfus9ENgvkN62znM4PnrlYf+kb+kliz7v6ymFC8nUo30iEC3sjPR7lBgAun2fJgB9K/+wLk71QNz7vPl7s3tR1xU/WsUFvB9Z+MIv2YrzK6g4/AnUXZIW7XGt2uyIOfbhrrqssCdx1doG/uyaXFXk8oXb6z+1kzSsz9QLrFevoDQuB7Y0NpQBB2htt6yCeX7GtfDV/WauA1gqoMobELgecC+7sZS0kE6EK8j3ySk4xZxgy3thytgwcYJWEhq+T+zS7hCyvQ1iuMmDLrd0WmMgnbHuszLLad93PnrwHe65c2oNg+79wNdHxVoUdTnyUkFi3zqtNxWrMKqPuOmbbzvLpcsi6PMHKGS7P2fF2K0bFWzuUHQBsseJtW47Rl6EFibSr9MtKlcf+fjW4vnUrIbnUz2rCTRJFXfIa3XD4hi0U/CoyQDHd8CZ0sakLxcu7y/jWHSOVEri0wKp+Z5I2V9pCmHQIkMpgfXCwow+C8UWbzxHt34h/g0WrNzpj4d2NvZLVcftgfov02IxD8XRlMDfhzUNp2HbzvGHi5OC6U5zEBqxtlqjY+aLl3uQINBGFQAzoBEAC31GOdxYR+MkRkTiV+yuBNKkkPEV3pEhuo3cStd7T2SCKsjoJqOF/F4po6DSok+Ly+ld4o8aNA2HMi7TRuGJ5aVlS7BGFjHgPSAFOv+eLRtyzdW26gmq88SYoXKbKkm1vysYTYFrtCbHj7u0x5kD4u30hH+gQZR3hehKpjox7gFLflCZrGRzZAk4kQIoCrJW8MYjvnEpSIzHbDVCQJMx/vza32Gxe6lMxflhM2q18/yu2mJC6Ppkl0T3dZ3RKcyQGBZpiGA2NHOv+Ay6CSkWZgcPuNQ1/AuBosFA33ZOTsn45DB2v2HXt4UFBO9PXGxI9NvkNENYXE7/CaGo7GNA16dPSTDqm6cF5L0vl3IKVS868WjhV2iemiCY25Kr/qQQxrHbs/QSKAIwre7R+xvLBgtadIZZVs9awypJ4q4nbAEnS0dBNbkKnV2cgnVPeyeQHd3jognCkRR9inkf0+octJUWbPYn3TYOf+H38Syro43HcDT8vf+iScaBAjx0kY2a+SQ/D29kGQFNyLTjWi8kY3RLLZuy5rjwkVfPO8g82vNg6zoSzre5EP2D/MIN1vN7jLQeBKgW7o/1EqL6UIb8Gbux39jmPhk1XxFw27JqyRZ1maQrkHzp+zak0tZuc2u95XHuDawXpe9d9JZUV9wMklsECYX0svmvXsBEzqWAjchwARAQABiQI2BBgBCAAgFiEEg45eHfQwAhARnT/c+r7dqC6htMUFAmFQAzoCGwwACgkQ+r7dqC6htMUYAQ/7BnMK0x1z/SySZQxkkPOank3fjwBzHCSiM0WDgaG2Soqc5/uuQCVfF55oIPW+wLzltqPAvcNnOKe47PkJGRaHQyllkW+gFJ9QSvK+SWS4u4/QA/5hT7juEliJux42Gxl6trKtlQxyMIgTbmY1YNbJraoZTwWb+cqGf5mxhRGx++DWKbV0KZdw+NkQUIIO1Q8h+00m7dG1K7vSpVW1x3JFt/kOzgvLvoPmc1Xk2uspRT5Ebir5AB4G3REuPXr0hoty0DXE/9F6nicBBCaiwyHhanfaxDq7Bkespua265GAhAmnDDHFKfKvLNzhPEPLbMa3cc85g4embnhXEGhuXjfXVuGXFgW/e+nuQX75icF0pCJFVemBpx3PC9UTD10giPajc007qzfQ2WCzlDCzzr1typAR/YTpGVVQuzJCcIoP7JzegkVivU83swu+kqw8wOd25OIXqWZKLin3qqAZsG6TKlxSzQDTJ3YgHr7myqH3da272CAiSMNYzyiJxXz7zmS+cmTIRot1HYEzvJiNlXr+dSRxI+vrsojO7iGke0/yrOSFsHom2cHytzSaqTortnLEBRwEz3LsNvZr7FCPDzd97QL7oU5/KO8ygSN0R19NpArOs+xRObwnBhV8ecYrYcWkj6QrJ3n4bytGTxkS413sIqUNb1fKUyc67raFMT55Hlw==KwYj END PGP PUBLIC KEY BLOCK. Notes: Node size indicates a market’s in degree. So, straight from the Market section click on ‘Market’ in the top left you’ll be presented with a selection of of featured items. A Guide to the Silk Road Dark Web. As such, they are not subject to reporting requirements or oversight from any government organization. It wraps your communications in 256 bit AES encryption to stop others from peeking at your messages or stealing sensitive information. Deep Web Radio is the dark web’s 24/7 onion radio link. If a hostname file is in the folder, we can check that it matches our desired address with the following command. The rendezvous point makes one final verification to match the secret strings from you and service the latter also comes from you but has been relayed through the service. Much of the decline was attributed by researchers at blockchain analysis firm Chainalysis to the shutdown of Hydra Market, which was taken down by law enforcement agencies in Germany and the U.

User manual
To stay safe while browsing dark web sites, follow these general rules. In addition, we also take note of the small samples of recent research adopting similar approaches, including the largest sample of qualitative interviews being 13 vendors selling drugs on these platforms Martin et al. Irrors: Germany, Worldwide, UK, EU. Indeed, this same economic calculus has been found to underlie the decision making of actors on digital platforms, including the decision to transition to online markets from offline markets, where profits are viewed as higher and risks as lower Décary Hétu and Giommoni 2017; Martin et al. Understanding PGP usage in this context is important, but can be overwhelming for newcomers. We will update with new links as needed. This outcome may be due to the threat actors being unable to profit from the Infinity Forum or achieve as much growth as they would like. Location wise it sort of depends on where you are. This provides potential clues on who could be buying or selling the shares, especially if the brokerage firm has a few clients, or it’s a firm that trades its capital. USDT goes live on NEAR Protocol, making it the 14th blockchain network to support Tether. Some vendors specialize in enterprise focused services. Those accessories were originally meant for just my larger bar soaps. No child porn is permitted in the market, and that is it. The rapid growth of layer 2 scaling solutions has been accelerated by the emergence of new rollup stacks like OP Stack, Polygon CDK, and Arbitrum Orbit as well as the abstraction of functionality into specialized layers. Results showed that the top ranking hidden web services are mostly famous in Tor network. No relationship is created with you, nor any duty of care assumed to you, when you use this blog. Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity. As mentioned in Subsection 4. KWADRON Cartridge System 0.
Twitter Feed
Why on earth would you use a vpn to connect to Tor. Delft University of Technology. The DAX index in Europe was at 5,621 up +2; the FTSE UK currently is 5,244 up +10. While the network statistics allow us to describe patterns in vendor flows, the use of ERGMs allows us to test 1 the mechanisms that drive the formation of the market networks and 2 the impact of a law enforcement interdiction on disrupting the structure of vendor flows between markets. Inspiration, strategy, and industry trends for makers and product designers on the move. 9500 Gilman DriveLa Jolla, CA 92093 0508United States619 534 2405 Phone619 534 7040 Fax. At the same time, renewable generators increasingly look for financial security by closing long term PPAs which take volume out of the spot markets. 2 by special agents of U. The ever evolving cryptocurrency market has grown exponentially over the last couple of years, and the industry is only continuing to expand. And most onion search engines operate as nonprofits and don’t display ads. An evolution of the Tor protocol is proposed to speed up the Tor Hidden Services. “But the global law enforcement community has innovated and collaborated to disrupt these ‘dark market’ websites, no matter how sophisticated or far flung they have become. Fresh working dark web links updated in 2023. Police crackdowns, as is the case for traditional drug markets, are not effective measures to lower the volume of sales on online illicit drug markets. So, what’s driving that downturn. We measure our dependent variable at two time points, 1 month before the seizure of DarkMarket pre seizure network and 1 month after the seizure of DarkMarket post seizure network. The commodity currencies are weaker this morning, CAD 0. Blockchain intelligence tools like TRM can be used by law enforcement and regulatory partners to identify counterparties and cashout points used by DNM proprietors, with the goal of obtaining documentation from those counterparties in order to potentially identify the proprietors, their virtual currency holdings, their infrastructure, and their locations. There is no hard evidence that such an interception occurred, but for sure, D. The “dark market” websites were designed to facilitate illicit commerce by providing anonymity to users. Peter Loshin, in Practical Anonymity, 2013. Disclaimer: This page may contain affiliate links. I’m not sure what the technical limitations of rendezvous eavesdropping are, but if it were possible to capture. A host is basically a website’s house, or where it lives and takes up space. There are some fascinating “hacker for hire” listings and services on Nemesis, as well as some malware and data dumps. Attorney Stephanie M. Conspicuously absent are some preferred features, such as the lack of pre order direct pay purchases, a multi sig option for BTC payments, and forced PGP encryption for communications. If you want to access regular HTTPS websites on the surface web via the Tor network for added privacy and anonymity, DuckDuckGo is what you need. Starting in or about November 2015, Pavlov is alleged to have operated a company, Promservice Ltd. We will continue to investigate, expose, and take action against criminal networks no matter where they operate.